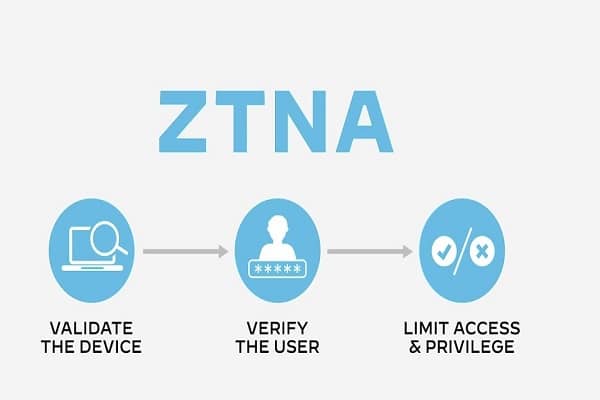
Zero accept as true with community get entry to (ZTNA) is a products or services that creates an identity- and context-primarily based totally, logical get entry to boundary round an software or set of packages. The packages are hidden from discovery, and get entry to is constrained through a accept as true with dealer to a fixed of named entities.
Contents
Verification
The dealer verifies the identity, context and coverage adherence of the desired individuals earlier than permitting get entry to and prohibits lateral motion somewhere else within side the community. This gets rid of software property from public visibility and extensively reduces the floor vicinity for attack.
Manage policies
Zero Trust Network Access (ZTNA) is a class of technology that gives stable far flung get entry to packages and offerings primarily based totally on described get entry to manage policies. Unlike VPNs, which furnish entire get entry to a LAN, Zero Trust network access answers default to deny, presenting most effective the get entry to offerings the person has been explicitly granted. It is vital to recognize the safety gaps and advantages ZTNA answers can offer businesses as extra far flung customers be a part of the community.
How ZTNA works
With ZTNA, get entry to is mounted after the person has been authenticated to the ZTNA provider. The ZTNA provider then provisions get entry to the software at the person’s behalf thru a stable, encrypted tunnel. This offers an introduced layer of safety for company packages and offerings through protective in any other case publicly seen IP addresses. Like Software Defined Perimeters (SDP), ZTNA leverages the idea of a darkish cloud, stopping customers from seeing any packages and offerings that they don’t have permission to get entry to. This introduces safety towards lateral attacker motion, wherein endpoint or credentials might in any other case allow scanning and pivoting to different offerings.
Access Control
Identity-primarily based totally authentication and get entry to manage located in ZTNA offerings collectively offer an opportunity to IP-primarily based totally get entry to manage commonly used with maximum VPN configurations. ZTNA additionally lets in businesses to put in force region or tool-particular get entry to manage policies, to save you un patched or inclined gadgets from connecting to company offerings. This alleviates not unusual place VPN-associated demanding situations wherein BYOD far flung customers are granted the identical degree of get entry to as customers at a company office, regardless of the truth that they regularly have fewer protection controls in place. Some agent-primarily based totally ZTNA answers offer a pre-authentication accept as true with evaluation of the connecting person and tool, consisting of tool posture, authentication status, and person region.
Visibility & Control with SASE
Like SDP however, ZTNA does now no longer offer inline inspection of person site visitors from the software after the person establishes a connection. This can cause capacity protection troubles while a person’s tool or credentials end up compromised, or within side the case of a malicious insider who makes use of their get entry to a aid to disrupt the software or host.
Security
Secure get entry to provider edge (SASE) answers that comprise ZTNA identity-primarily based totally authentication and granular get entry to manage abilities offer a extra entire, holistic approach. SASE answers offer the cloud scalability, protection and community abilities required for stable far flung get entry to management. But in contrast to standalone ZTNA answers, SASE offers post-join tracking for symptoms and symptoms of statistics loss or compromised credentials.
Also read: 4 Reasons Cyber Security Is Crucial For Anyone’s Safety Now More Than Ever
Learn extra approximately how a SASE solution, collectively with ZTNA can offer each safety and get entry to manage in your corporation on this blog.